Aws S3 Security Breach

Today we are releasing a new cloudgoat scenario cloud breach s3 which is.
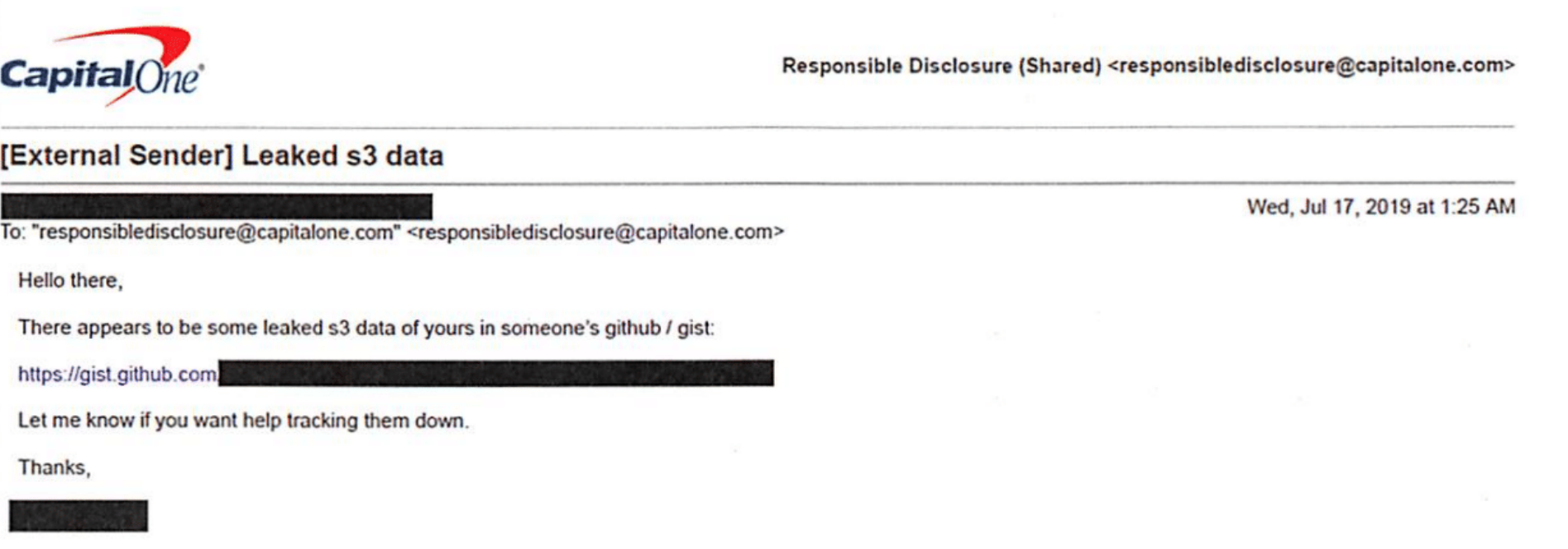
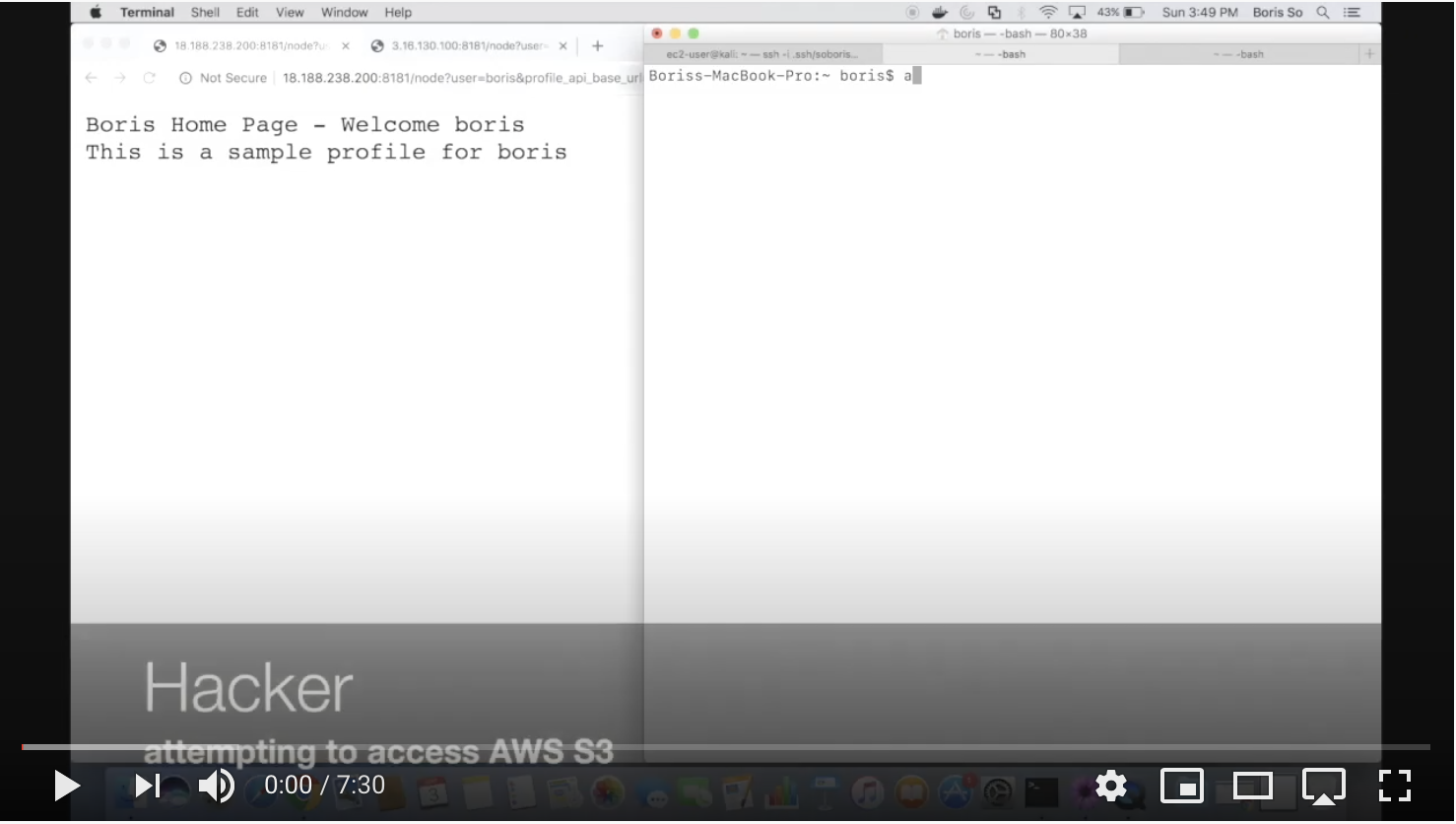
Aws s3 security breach. Learn from the examples of corporations including accenture timer warner cable and uber. Over 106 million people affected. On july 19th 2019 capital one got the red flag that every modern company hopes to avoid their data had been breached. Aws subscribers should learn to how to avoid potential breaches by implementing the the methods listed here.
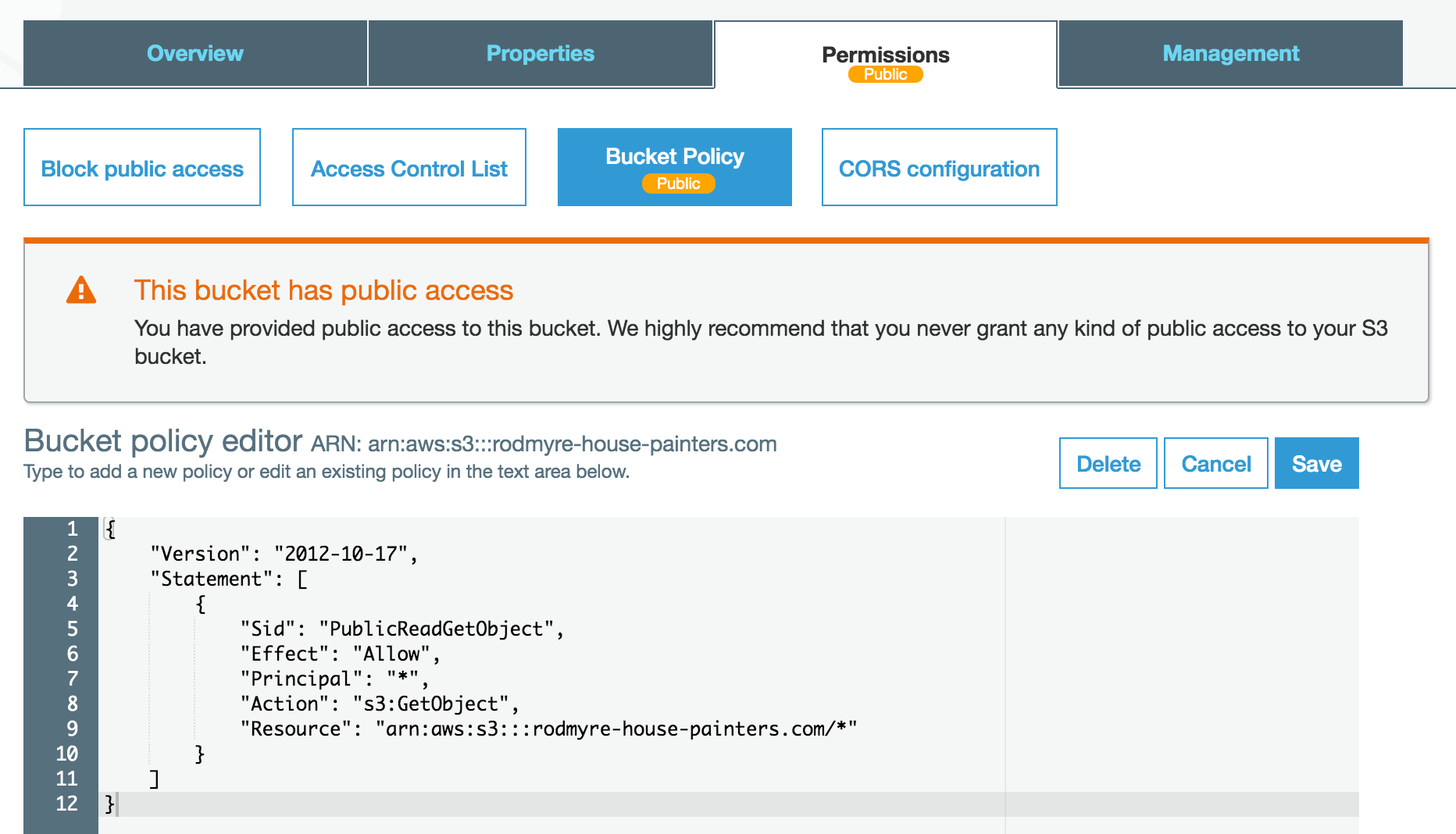
That fact is made abundantly clear by the growing number of incidents caused by extremely poor security hygiene within amazon simple storage service s3 storage buckets that are holding very sensitive information. 140 000 social security numbers. The type of misconfiguration that allowed for this security breach is seen so often in aws penetration tests by rhino security labs researchers that it was included at the re launch of cloudgoat 2 during re inforce as one of the scenarios. Following notification to amazon web services aws and the uk s national cyber security centre.
While many organizations work hard to secure data stored on cloud stores the truth is that there s a lot of work to go. This scenario titled ec2 ssrf can be found on our github here. The rash of data breaches related to s3 exposures is a salient point which highlights the burgeoning security debt. An aws spokesman confirmed that the company s cloud had stored the capital one data that was stolen and said it wasn t accessed through a breach or vulnerability in aws systems.
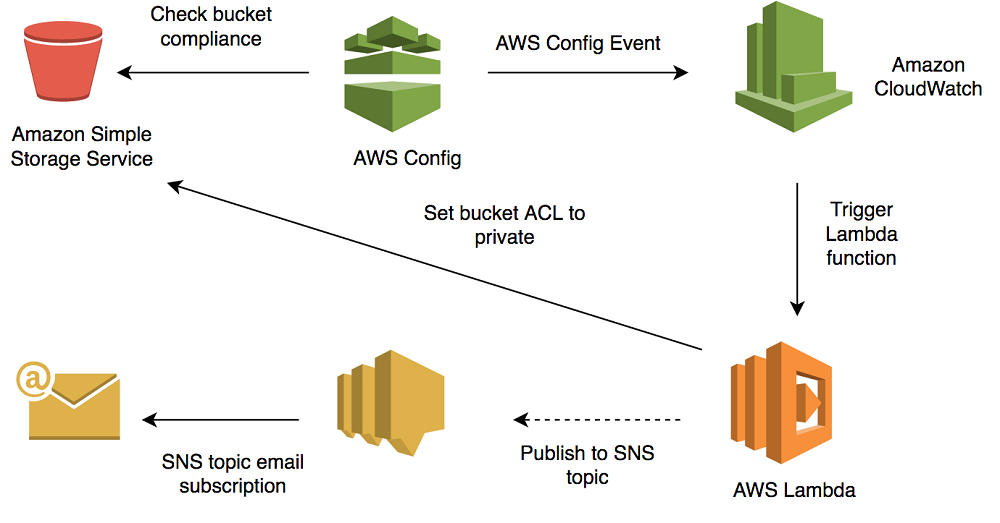
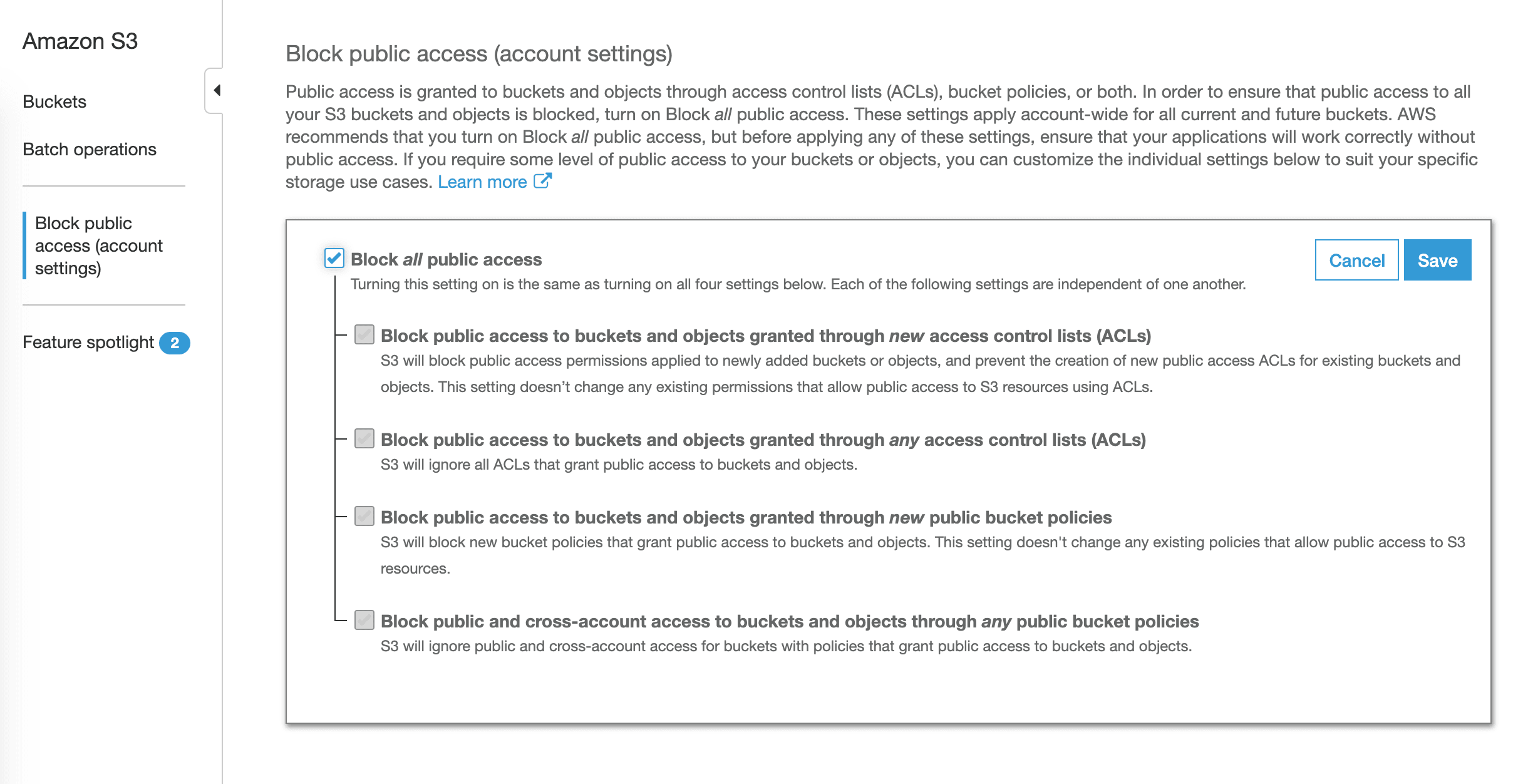
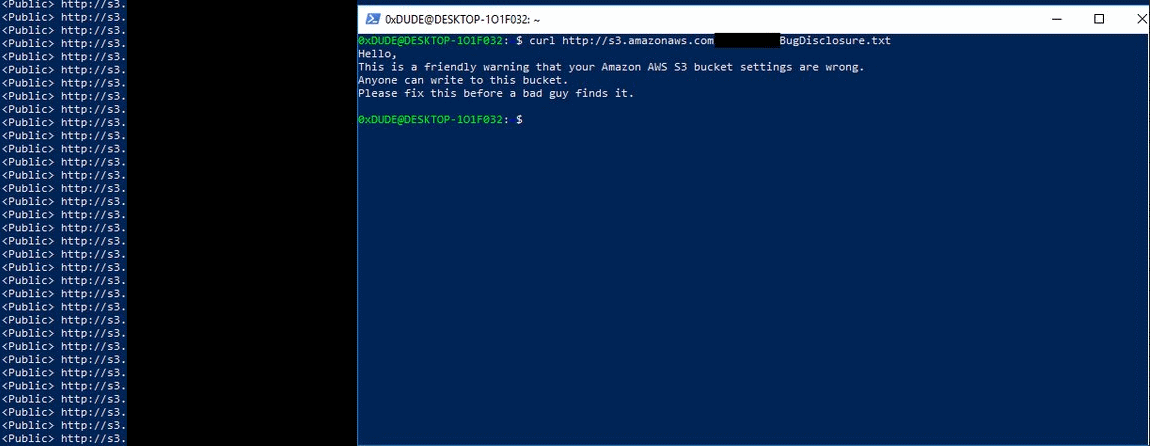
Jeff barr chief evangelist for amazon web services recently announced public access settings for s3 buckets a new feature designed to help aws customers stop the epidemic of data breaches caused by incorrect s3. 80 000 bank account numbers. A common reason for not taking advantage of public cloud computing was security concerns. How to beef up s3 bucket security to prevent a breach.
According to rob enns vice president of engineering for bracket computing the prevalence of the s3 breaches highlights the fact that organizations must own their cloud security they cannot. Over four years upguard has detected thousands of s3 related data breaches caused by the misconfiguration of s3 security settings.